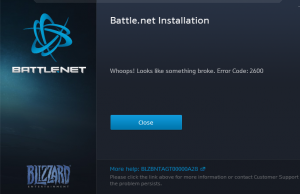
Recently I tried to install the latest patch for Heroes of the Storm when I got a nasty error code 2600, Whoops! something broke.
Re-installing battle.net didn’t fix the issue. After much frustration I came across this post, which describes situations when you’re behind a caching proxy (which I am.)
I did as it directed, which is to disable the caching function of my proxy and delete anything Blizzard-related from my %temp% folder.
That did the trick. All is well now!
Update: I decided that rather than disabling caching / virus checkings completely I would create an exception in Sophos UTM web access policy. Thanks to the guidance from here I added the following exception:
| blizzard |
| Skipping: | Authentication / Caching / Block by download size / Antivirus / Extension blocking / MIME type blocking / URL Filter / Content Removal / SSL scanning / Certificate Trust Check / Certificate Date Check |
| Matching these URLs: | ^https?://([A-Za-z0-9.-]*\.)?blizzard\.com/ ^https?://([A-Za-z0-9.-]*\.)?blizzard\.vo\.llnwd\.net/ ^https?://([A-Za-z0-9.-]*\.)?blizzard.com\.edgesuite\.net/ ^https?://([A-Za-z0-9.-]*\.)?battle\.net/ |